Mikrotik RB250GS - 5 Port Gigabit Switch
Saturday, November 5, 2011
0
comments
This little Mikrotik has the same form factor as the 750/750G. It is a 5 porter that I was able to get your standard gigabit speeds through…nothing remarkable there. So why should I buy one?
First, they are shipped to your door for around $40. Not a bad price for a small managed gig switch.
 Second it has some interesting features
Second it has some interesting features  It runs a new OS called Switch OS, SwOS(here’s the wiki on it).
It runs a new OS called Switch OS, SwOS(here’s the wiki on it).
SwOS is only accessible via a web browser. My switch came shipped with OS v1.0. I went ahead and installed 1.1. When upgrading from 1.0 you upload the new OS, then hard reboot the switch. When it comes back up it will be running the new version.
On the system setting there is no entry for subnet mask or default gateway. The switch will simply respond to whatever IP contacts it. What this tells me is that the switch can’t dump any messages out…I really wanted syslog messages out of this guy. It is, however, accessible via SNMP.
Link Screen:
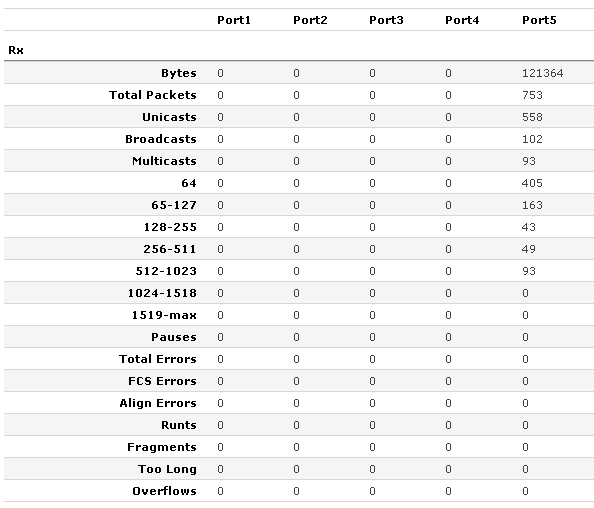
It doesn’t appear as if you can manipulate the MTU on the switch, which probably means no jumbo frame support(*This will be added in version 1.2 with MTU up to 9000*)…which is something I’ve come to expect from a managable gig switch. As a side note, when pinging the switch a max MTU into the CPU of the switch is 1272…not important, but interesting. Statistics Screen:
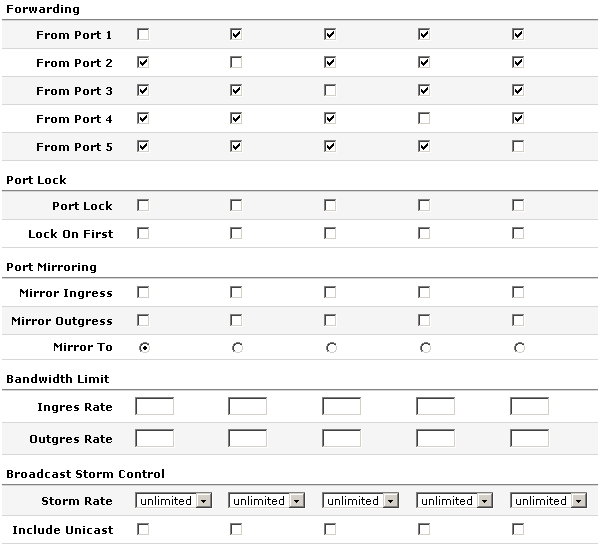
The status screen covers standard errors, counters on broadcast and unicast, but has some additional entries not commonly seen. It keeps counters on packets of varying sizes as well as fragments. Forwarding Screen:
The forwarding section allows you to limit which ports can communicate with other ports. Somewhat like Cisco’s private VLANs.
Port lock prevents MACs from being learned on a port (you would need to do manual entries). Lock on first option allows the switch to only learn the first mac that shows up on the port. This would only be useful for users without IP phones.
Standard mirroring.
Bandwidth limit…I LIKE THIS FEATURE! Hardware rate limiting is missing from a lot of low end manageable switches. The values are expressed in bps.
Storm control, both broadcast and unicast. This is represented as about 20 options ranging from 1k to 1 million.
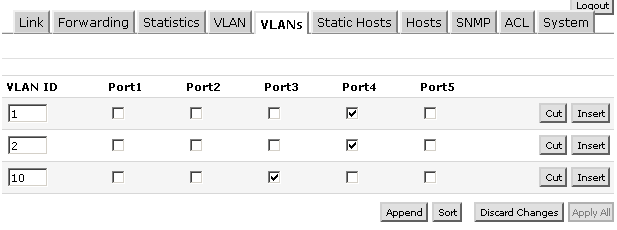
VLANs Screen:
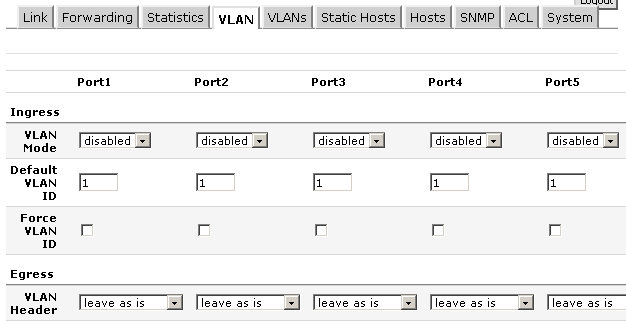
This screen basically creates the vlan database. The ports you check on this screen send the tagged packets down these ports…you are telling the switch which ports are trunked and what vlans traverse these trunks. These are tagged ports. You don’t need to set a tag on ports that will only be access. VLAN Screen:
This page is where you configure ports to trunk or be access.
Vlan modes vary. You can accept tagged packets. You can drop untagged packets. You can remark all packets with different vlan tag. You can accept untagged packets into the native vlan. Pretty robust feature set. To have a trunk port first define the vlans in the vlans section, then here on the vlan screen set the port to enable or some derivative.
If you want a standard access port set the default vlan to the vlan you want the traffic to head to, set the mode to strict, then set the vlan header to “add if missing”.
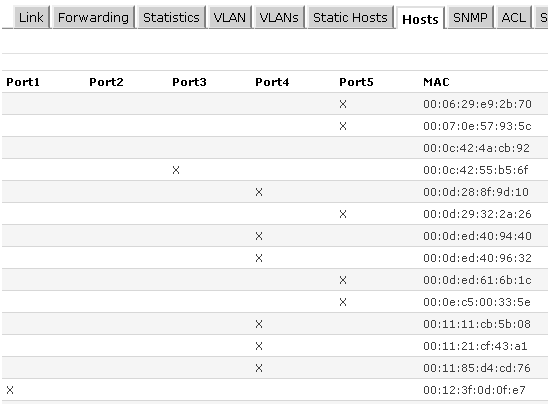
Hosts Screen:
ACL Screen:
This is a filter table. You can get pretty crazy with this thing. You set specific ports that macs/ip addresses are allowed to be sourced from or travel to. If you want to drop a source mac, specify the mac address, then hit the redirect check box, but don’t specify an interface. Another interesting thing to note is the fact that there is the option to on the fly set or reset the VLAN ID of a frame to whatever you want…pretty wacky. If you could also specify a port you could do some DHCP filtering…which would be NICE. Some DHCP rogue mitigation would be nice.
This would make for a decent little switch with gig speeds. It has some interesting features, though I would like to see some spanning tree and syslog exporting. I also like how it shows up in Mikrotik neighbors.
What features would you guys like to see/what would you guys like to use this for?
(http://gregsowell.com/?p=2063).
First, they are shipped to your door for around $40. Not a bad price for a small managed gig switch.
 Second it has some interesting features
Second it has some interesting features SwOS is only accessible via a web browser. My switch came shipped with OS v1.0. I went ahead and installed 1.1. When upgrading from 1.0 you upload the new OS, then hard reboot the switch. When it comes back up it will be running the new version.
On the system setting there is no entry for subnet mask or default gateway. The switch will simply respond to whatever IP contacts it. What this tells me is that the switch can’t dump any messages out…I really wanted syslog messages out of this guy. It is, however, accessible via SNMP.
Link Screen:
It doesn’t appear as if you can manipulate the MTU on the switch, which probably means no jumbo frame support(*This will be added in version 1.2 with MTU up to 9000*)…which is something I’ve come to expect from a managable gig switch. As a side note, when pinging the switch a max MTU into the CPU of the switch is 1272…not important, but interesting. Statistics Screen:
The status screen covers standard errors, counters on broadcast and unicast, but has some additional entries not commonly seen. It keeps counters on packets of varying sizes as well as fragments. Forwarding Screen:
The forwarding section allows you to limit which ports can communicate with other ports. Somewhat like Cisco’s private VLANs.
Port lock prevents MACs from being learned on a port (you would need to do manual entries). Lock on first option allows the switch to only learn the first mac that shows up on the port. This would only be useful for users without IP phones.
Standard mirroring.
Bandwidth limit…I LIKE THIS FEATURE! Hardware rate limiting is missing from a lot of low end manageable switches. The values are expressed in bps.
Storm control, both broadcast and unicast. This is represented as about 20 options ranging from 1k to 1 million.
VLANs Screen:
This screen basically creates the vlan database. The ports you check on this screen send the tagged packets down these ports…you are telling the switch which ports are trunked and what vlans traverse these trunks. These are tagged ports. You don’t need to set a tag on ports that will only be access. VLAN Screen:
This page is where you configure ports to trunk or be access.
Vlan modes vary. You can accept tagged packets. You can drop untagged packets. You can remark all packets with different vlan tag. You can accept untagged packets into the native vlan. Pretty robust feature set. To have a trunk port first define the vlans in the vlans section, then here on the vlan screen set the port to enable or some derivative.
If you want a standard access port set the default vlan to the vlan you want the traffic to head to, set the mode to strict, then set the vlan header to “add if missing”.
Hosts Screen:
ACL Screen:
This is a filter table. You can get pretty crazy with this thing. You set specific ports that macs/ip addresses are allowed to be sourced from or travel to. If you want to drop a source mac, specify the mac address, then hit the redirect check box, but don’t specify an interface. Another interesting thing to note is the fact that there is the option to on the fly set or reset the VLAN ID of a frame to whatever you want…pretty wacky. If you could also specify a port you could do some DHCP filtering…which would be NICE. Some DHCP rogue mitigation would be nice.
This would make for a decent little switch with gig speeds. It has some interesting features, though I would like to see some spanning tree and syslog exporting. I also like how it shows up in Mikrotik neighbors.
What features would you guys like to see/what would you guys like to use this for?
(http://gregsowell.com/?p=2063).